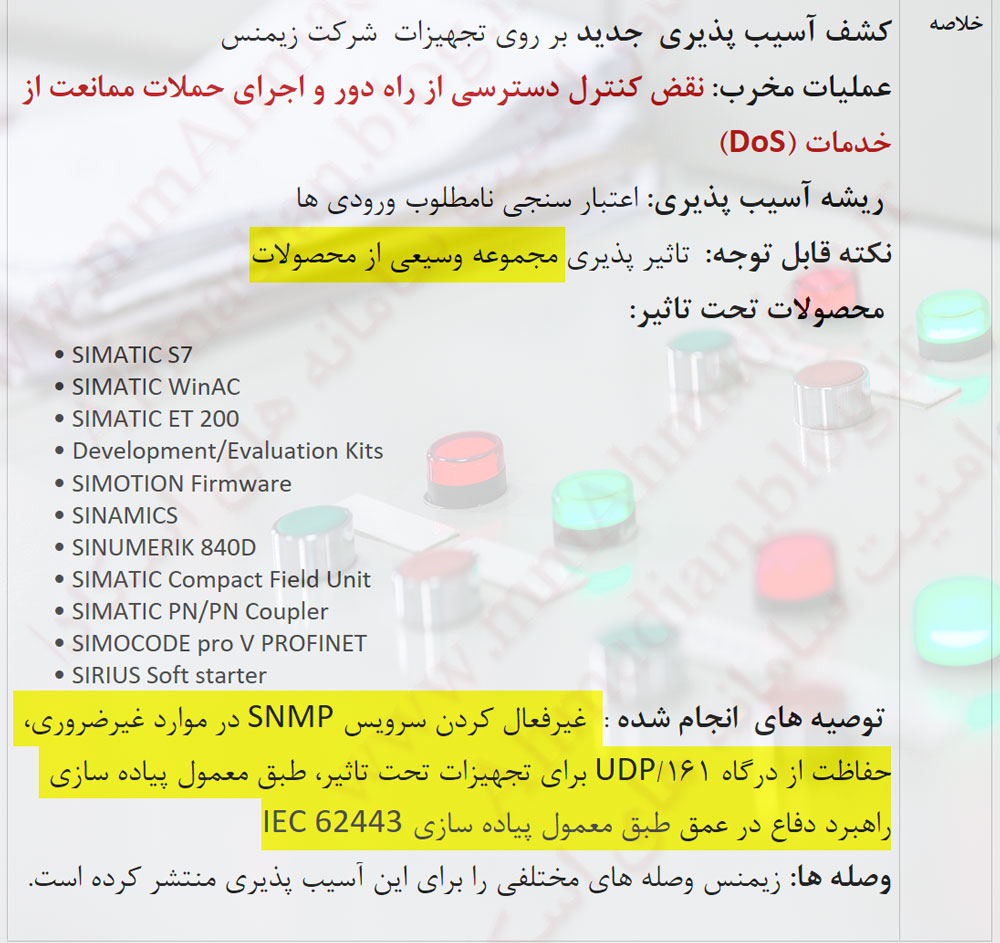
کشف آسیب پذیری جدید بر روی تجهیزات شرکت زیمنس
عملیات مخرب: نقض کنترل دسترسی از راه دور و اجرای حملات ممانعت از خدمات (DoS)
ریشه آسیب پذیری: اعتبار سنجی نامطلوب ورودی ها
نکته قابل توجه: تاثیر پذیری مجموعه وسیعی از محصولات
راهکارهای مقابله:
SIMATIC S7-200 Smart: Update to V2.03.01:
- SIMATIC S7-400 PN V6: Update to V6.0.6:
- EK-ERTEC 200P: Update to V4.5:
- SIMOTION D: Update to V5.1 HF1:
- SIMOTION C: Update to V5.1 HF1:
- SIMOTION P320-4: Update to V5.1 HF1:
Please contact a Siemens representative for information on how to obtain the update.
- SINAMICS G110M / G120(C/P/D): Update to V4.7 SP9 HF1:
Siemens is preparing further updates and recommends the following mitigations until patches are available:
- Disable SNMP if this is supported by the product (refer to the product documentation). Disabling SNMP fully mitigates the vulnerability
- Protect network access to Port 161/UDP of affected devices
- Apply cell protection concept
- Use VPN for protecting network communication between cells
- Apply Defense-in-Depth
Siemens recommends users configure the operational environment according to Siemens’ Operational Guidelines for Industrial Security:
For more information on the vulnerability and more detailed mitigation instructions, please see Siemens Security Advisory SSA-346262 at the following location:
NCCIC/ICS-CERT recommends that users take defensive measures to minimize the risk of exploitation of this vulnerability. ICS-CERT reminds organizations to perform proper impact analysis and risk assessment prior to deploying defensive measures.
ICS-CERT also provides a section for control systems security recommended practices on the ICS-CERT web page. Several recommended practices are available for reading and download, including Improving Industrial Control Systems Cybersecurity with Defense-in-Depth Strategies.
Additional mitigation guidance and recommended practices are publicly available in the ICS‑CERT Technical Information Paper, ICS-TIP-12-146-01B--Targeted Cyber Intrusion Detection and Mitigation Strategies, that is available for download from the ICS-CERT web site.
Organizations observing any suspected malicious activity should follow their established internal procedures and report their findings to ICS-CERT for tracking and correlation against other incidents.
No known public exploits specifically target this vulnerability.